7 Tenants of Zero Trust
A Zero Trust System is a security framework designed to protect organizations by assuming no entity—whether inside or outside the network—is inherently trustworthy. It enforces strict access controls, continuous verification, and least-privilege principles across all users, devices, applications, and data. Core components include verifying identity and context for every request, segmenting networks to limit lateral movement, encrypting communications, and monitoring systems continuously for threats. By treating every interaction as a potential risk, Zero Trust minimizes the attack surface, reduces vulnerabilities, and ensures robust, adaptive protection against modern cybersecurity threats.

Resource Definition
In a Zero Trust Security framework, a resource definition refers to the detailed identification and categorization of assets within a system, such as data, applications, services, or infrastructure. This includes specifying attributes like sensitivity level, access requirements, and protection mechanisms to ensure precise and secure access control.

Secure Communication
The practice of protecting data exchanged between systems, users, and devices through encryption, authentication, and integrity checks, ensuring that information remains confidential, tamper-proof, and accessible only to authorized entities.

Access To Resources Per-Session
A Zero Trust principle where access to resources is granted dynamically and temporarily for each session, based on real-time authentication and context, ensuring that permissions are not retained beyond the session’s duration.

Policy Defining Access To Resources
A set of rules that govern who or what can access specific resources, under what conditions, and to what extent, based on attributes such as identity, role, location, device security, and real-time context in alignment with Zero Trust principles.

Monitor and Measure Integrity & Security Posture
The continuous process of assessing and tracking the health, compliance, and security of systems, devices, and networks to detect vulnerabilities, ensure alignment with policies, and respond promptly to threats, maintaining a robust Zero Trust environment.

Authentication and Authorization Enforcement
The process of verifying the identity of users, devices, or applications (authentication) and ensuring they have the appropriate permissions to access resources (authorization), with strict enforcement at every access point in line with Zero Trust principles.

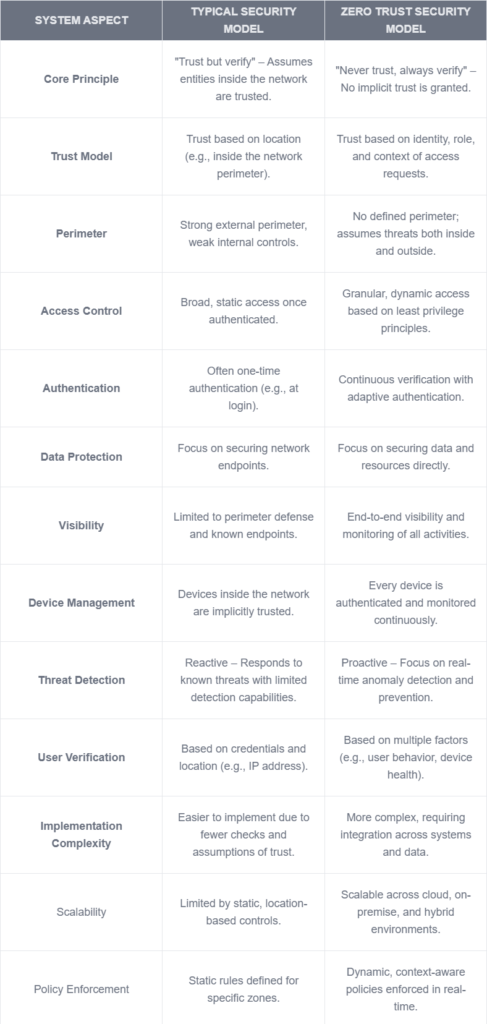
Zero Trust vs Typical Security System
The fundamental difference between a Zero Trust security model and a typical security system lies in establishing and maintaining trust. A typical security system operates on the principle of “trust but verify,” where entities within the network perimeter are considered trustworthy by default. This approach relies on a solid external boundary, such as firewalls, to prevent unauthorized access, but it often leaves internal systems vulnerable to lateral movement if the perimeter is breached. In contrast, Zero Trust adopts a “never trust, always verify” mindset. It assumes no user, device, or application should be trusted by default, regardless of whether inside or outside the network. Access is granted based on continuous authentication, granular policies, and real-time monitoring. This ensures strict least-privilege access and minimizes the risk of data breaches by comprehensively addressing external and internal threats. Zero Trust is particularly suited for modern environments with cloud-based resources and remote workforces where the traditional network perimeter is no longer sufficient.